How to successfully disable basic authentication on Microsoft 365 before end of life support
- Why Microsoft is ending Basic Authentication methods ?
- How to know if a tenant has users/devices using Basic Authentication
- Get a report with accounts using Basic Authentication on Microsoft 365
- Use a Web App to get daily reports on which devices are using Basic Authentication
- How to disable Basic Authentication for user groups in order to prevent new devices with legacy protocols
- How to postpone or re-enable legacy clients until December 2022
Update September 1st 2022: It's possible to postpone turning off basic authentication until December 2022 or re-enable basic auth protocols until the end of the year. Steps on how to do it here.
Microsoft/Office 365 will stop supporting what is called Basic Authentication after October 2022, this means that any client app/device using authentication methods on which is not possible to enforce MFA (multi-factor authentication) won't be able to login anymore (except Auth SMTP)
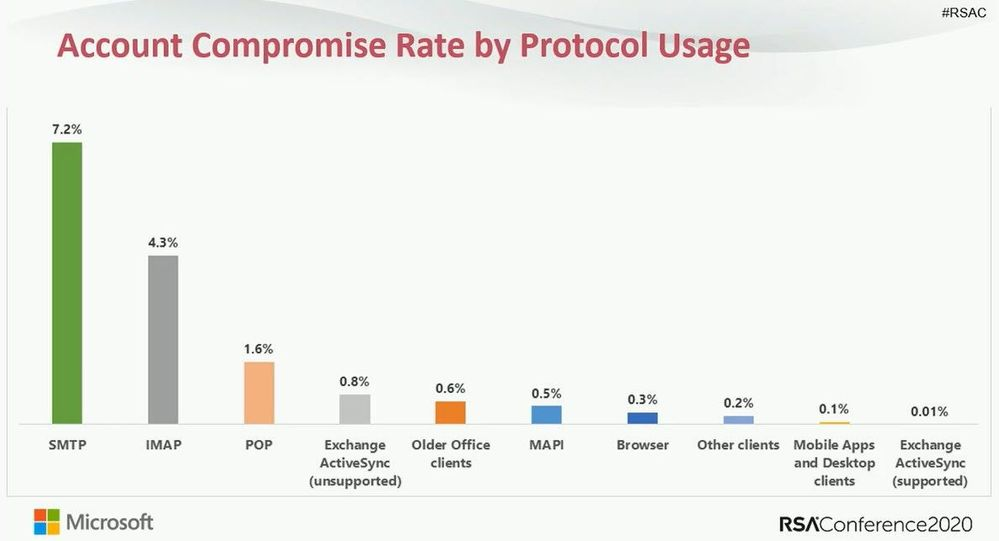
The main reason Microsoft decided to apply this security measures is related with the graph below, the most common source of emails sent through compromised accounts is stolen credentials using phishing attacks and logins through basic authentication methods. Basic authentication methods means the client device is connecting to the server through a channel which is not possible to enforce MFA.
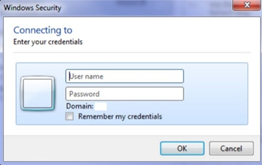
To keep things simple , this means moving all logins to the Web based prompt (Modern Authentication)
From this:
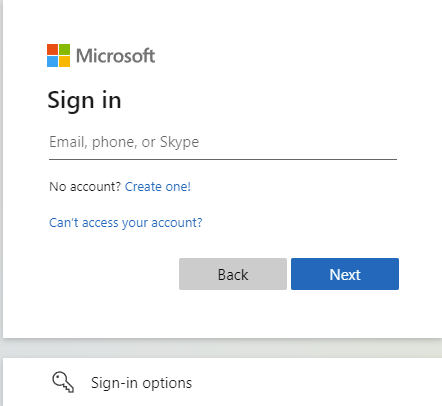
To this:
Is my tenant still using basic authentication ?
If your tenant is recent you might never had the option to use basic authentication because your
organization
security defaults were enabled which doesn't
allow the legacy method.
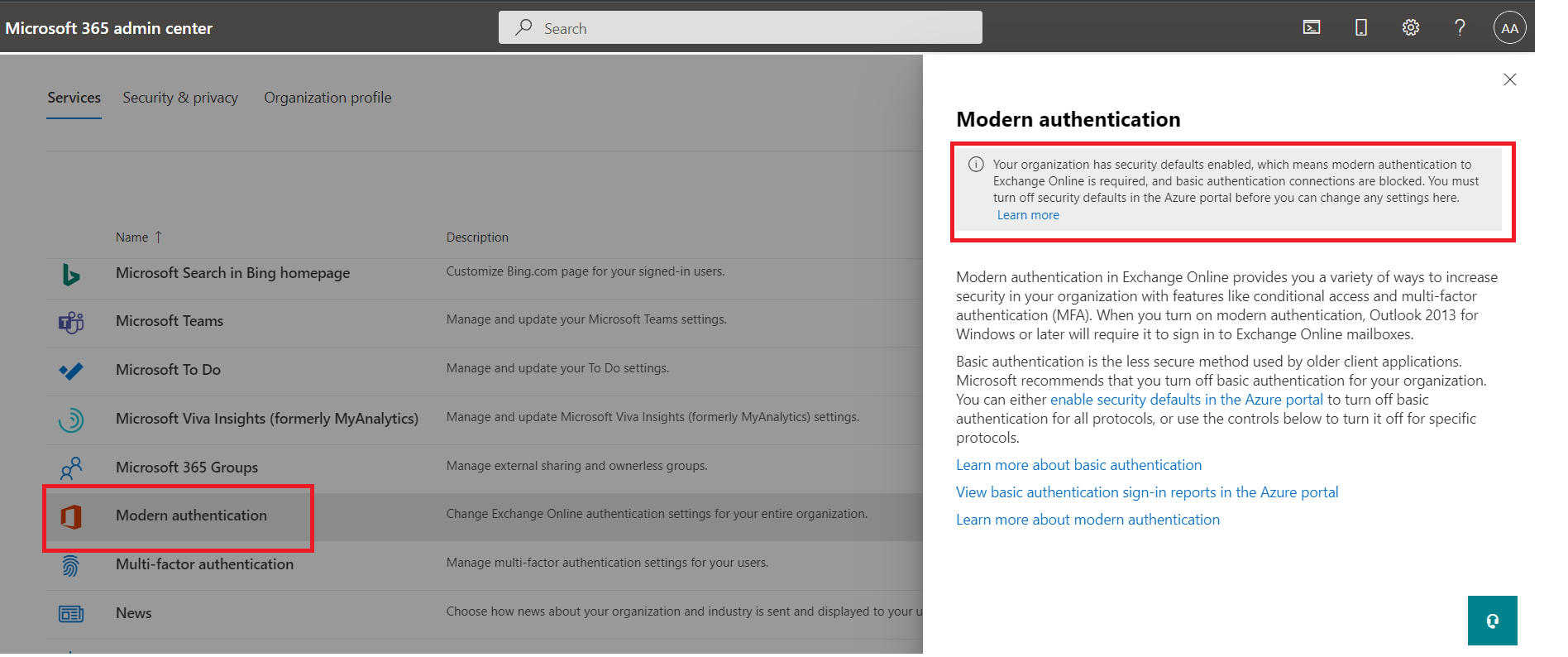
The easiest way to check is to go to your tenant admin page
, click Settings on the left side and then Org Settings. From the list click Modern
Authentication and depending on what you see from the
following images you can already have Modern Authentication forced:
Modern Authentication forced (nothing to do):
Tenant still allows Basic Authentication connections:
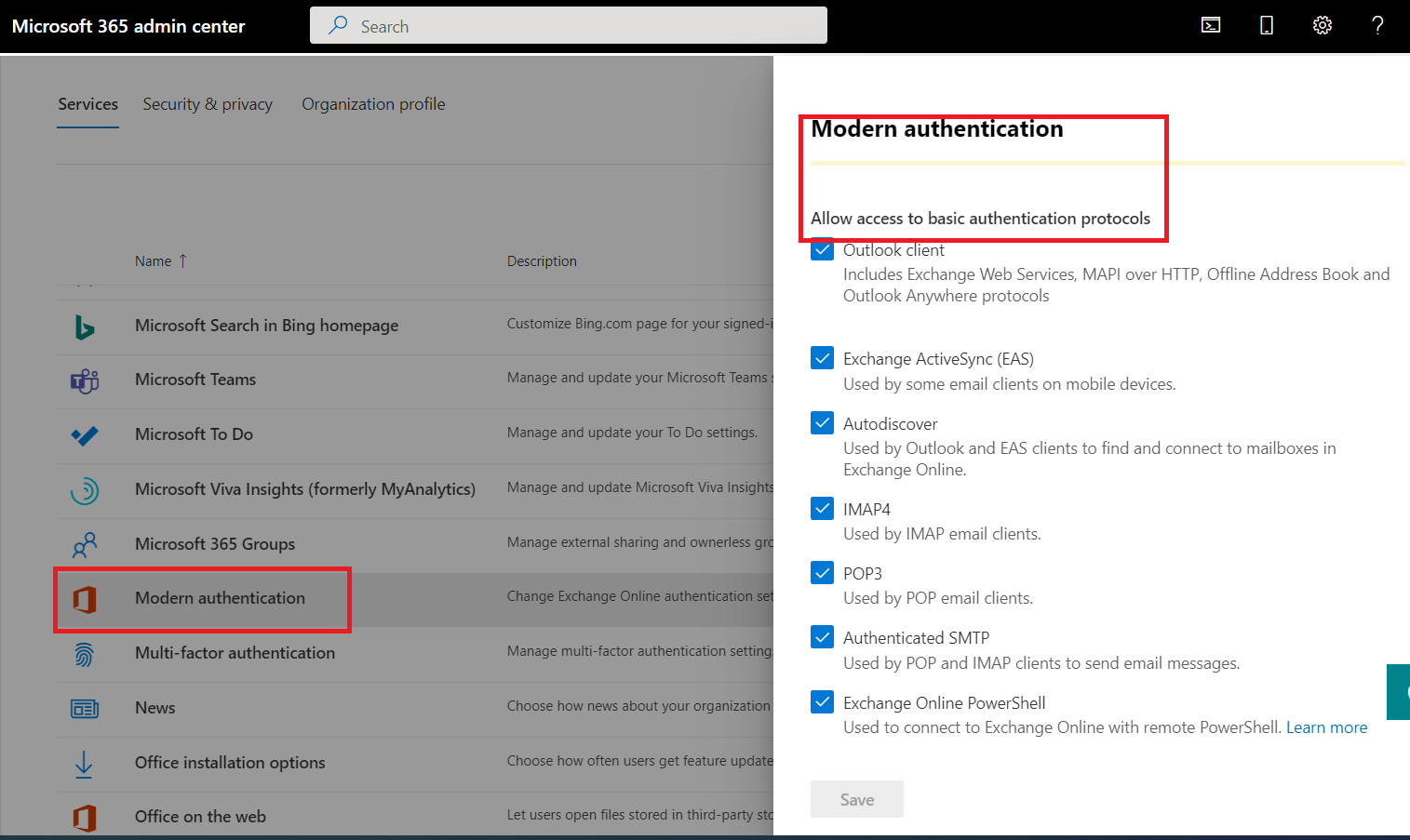
If your tenant still allows Basic Authentication then you need to check if there are any accounts/devices using it.
Find Microsoft 365 users/devices still using Basic Authentication Method
There are two methods to check which Sign-ins are using Basic Auth, either through Azure Active Directory Portal -> Users -> Sign-in logs or through a Web App we've implemented which sends you daily list of sign-ins using the end of life auth method.
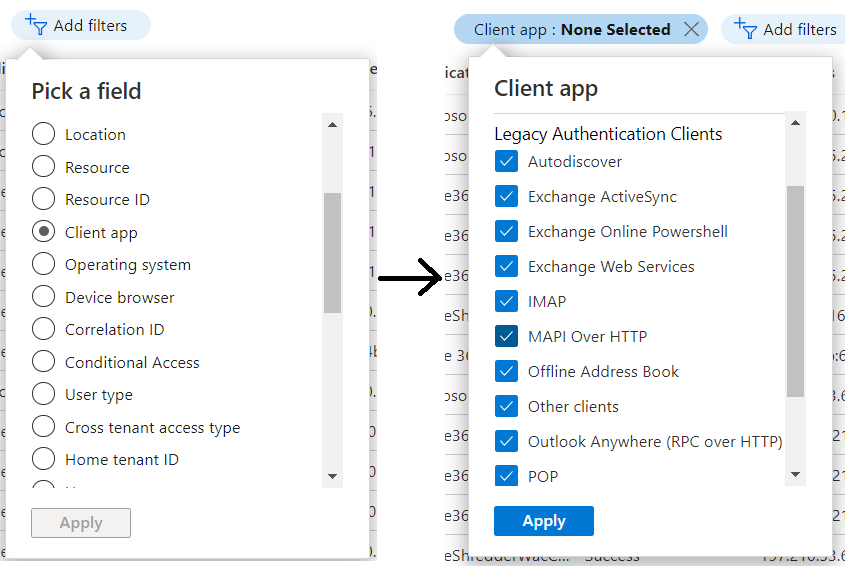
Using the Azure AD Sign-in logs:
- Go to the sign-in logs and click the Add filters
- Select Client app and click "Apply".
- Then click "Client app:none selected" and select all entries below "Legacy Authentication Clients" and click "Apply".
This will show sign-ins from users or devices using the Basic Auth method , which will stop working on October 2022, the list might not include all depending on the retention period your Azure Ad license supports.
Use a Web App which sends you a list of devices using the Basic/Legacy Authentication methods
We've implemented a Web App which you can access here, which analyses the sign-in logs regularly and checks which devices/users are connecting to your Azure AD using the end of life authentication methods. You can choose to receive either a weekly or daily report with the list of clients using basic authentication directly to your email.
In order to understand if a sign in represents a new device for a user we store an encrypted hash of
the user email on our Database. We don't use it for anything else except to check if the sign in
came from a new device which needs to be configured to use Modern Authentication.
All
data is deleted either at your request or reaching November 2022 when Microsoft plans to have
disabled Basic Authentication from Microsoft 365 tenants.
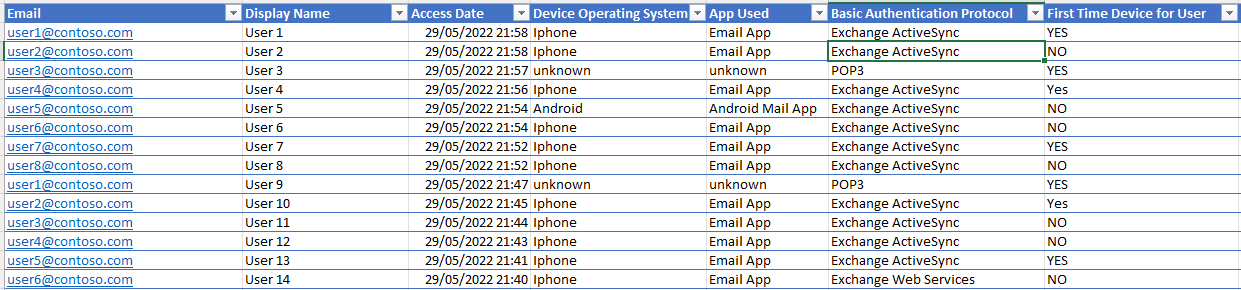
You receive through email an Excel file similar to the image below with a list of users, respective email and which device/app are using the basic authentication. We also send for each situation links suggesting on how to migrate the device/user to Modern Authentication (the data is just for illustration purposes).
I've migrated the devices and users which were still using Basic Authentication, how can I prevent new ones from using it ?
After providing instructions to users on how to migrate their devices to Modern Authentication your tenant should prevent those users from adding new devices through legacy authentication.
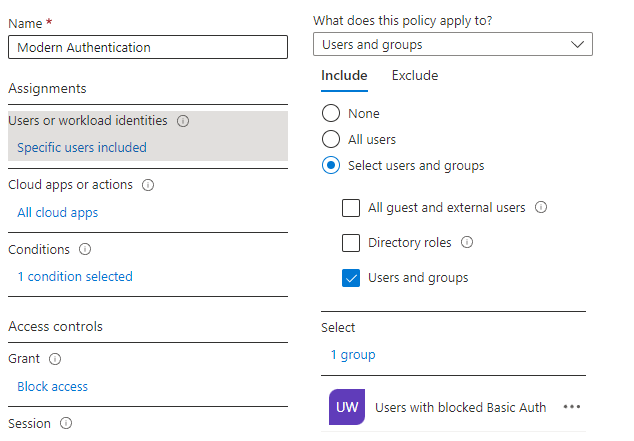
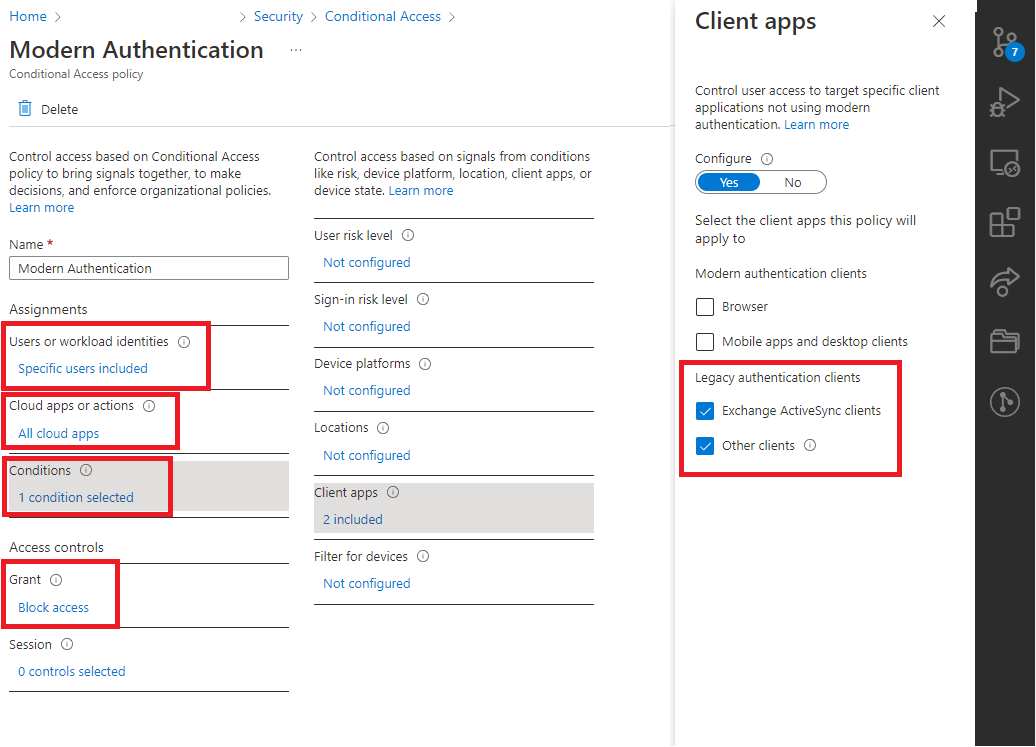
To achieve this we are going to create a new Group and use it in Conditional Access:
- Under your Tenant Admin page create a new Group called Users with blocked Basic Auth
- Open Conditional Access under Azure Active Directory -> Security
- Under "Policies" click "New Policy" to create a new one
- Call it "Enforced Modern Authentication"
- In "Users or workload identities" specify which Group should be included. Under "Include" tab
select the newly created group Users with blocked Basic Auth
- Under Cloud apps or actions make sure Include -> App cloud apps is selected
- Under Conditions select Client apps and select the legacy authentication clients
- In Grant select Block Access
- Finally make sure Enable Policy at the bottom is set to On
Microsoft just gave tenant admins the option to postpone the "turn off" date to December
In a blog post from September 1st Microsoft stated tenants that haven't moved all devices to Modern Authentication can preemptive postpone the "cut off" date from October to December but not later than January 2023
Bellow follows a quick summary of the different options tenant admins have with this new change, meanwhile you can give our Web App a try to find legacy clients that must be moved to Modern Authentication.
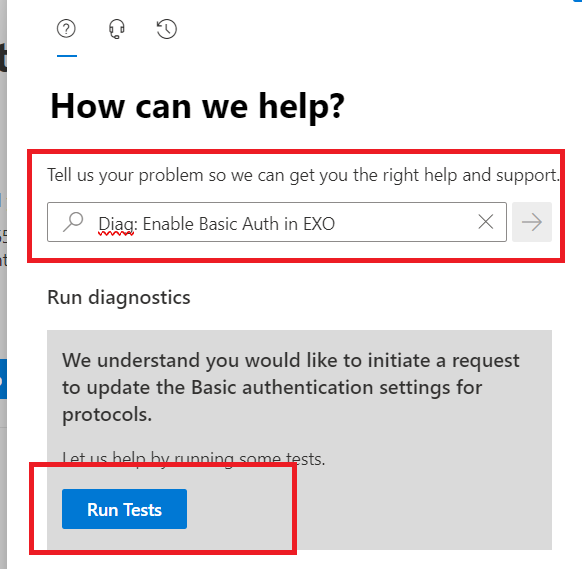
If you execute the following steps before October 1st the basic authentication protocols will only be disabled in December if you do it after October 1st the legacy clients will be re-enabled until December. In January 2023 there is no "second chance".
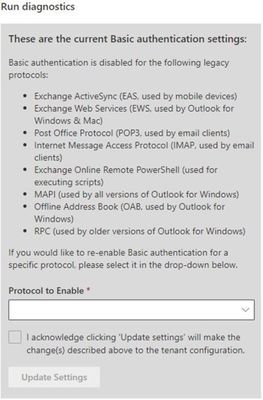
- Access the tenant admin page through this link or on the admin page open the "support request" dialog and submit the help request "Diag: Enable Basic Auth in EXO"
- Click in "Run Tests"
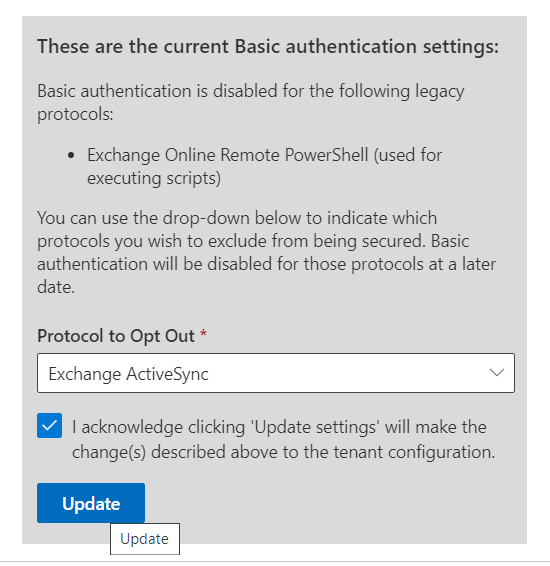
- Finally select which basic authentication protocols you'd like to keep active until December
and click Update
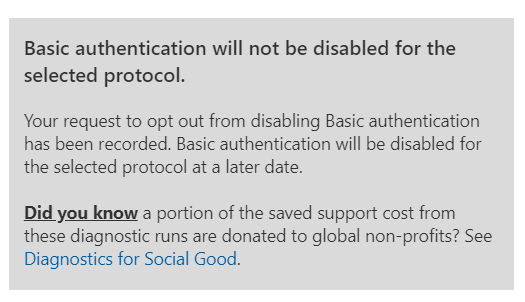
- The next image is what you'll see if you run the steps after the basic authentication protocols were already disabled
How to handle specific devices using basic authentication can be found on our next post